According to Viswanath Ramaswamy, the Vice President of IBM Technology Sales and IBM India/South Asia, "cyber-attacks are the biggest challenge to enterprise cyber-resilience in India". Ramaswamy also goes on to say that the three factors that majorly contribute to the (multi-party) costs incurred by companies due to data breach-related cyber-attacks are
with stolen/compromised credentials, phishing, and accidental device and data loss being the primary initial (human in the loop) attack vectors triggering the data breach cyber-attacks (including ransomware as the currently most popular type). The result is that enterprise cyber-attacks are evolving into market stressors that are hurting the Indian economy, where businesses are passing on the costs of data breaches to end users (consumers) as a form of a "cyber-tax".
A major issue most IT/IoT-driven enterprises in India face today concerning sustaining enterprise cyber-resilience (i.e., maintaining BC of salient processes and components at a minimum acceptable service level) in the face of a fast expanding cyber-threat space is that it takes on average 280 days to detect and contain a breach (350 days if more than 50 percent of work of an organisation is done remotely) and 315 days on average to do the same for a malicious breach (based on IBM data from 500 enterprises during the period 2018-2020).
In addition to this, less than 35 percent of cyber-security expertise slots are filled up, out of which some are entry-level security analysts who take time to develop the skills, confidence, and intuition to investigate data breach cyber-attacks.
Moreover, on the psychological front, many cybersecurity personnel suffer from job fatigue. This is due to
Adds to solution integration/synthesis complexity for cybersecurity personnel, especially when a new and advanced cyber threat arrives.
Finally, it is well-documented and widespread knowledge that approximately 95 percent of enterprise cyber-breaches are initially rooted in "human in the loop" issues.
All these factors add up to the likelihood that a cyber-security expertise team within an enterprise would be an important indicator of enterprise compromise by cyber-attack vectors. According to the IBM Security Data Breach Report of 2022, an Indian enterprise, on average, can save Rs10 crore (approximately $1.2 million) if it can detect a cyber breach in less than 200 days compared to when it detects in more than 200 days.
Enter Artificial Intelligence as a "Tool" to Boost Enterprise Cyber-Resilience
Artificial Intelligence (AI) can alleviate all the above issues, acting as a barrier to improved cyber-resilience in the following FOUR ways when compared to human intelligence solely.
1. To start, AI has the power to automate repeatable tasks, contributing to lesser fatigue of personnel/employees in enterprise security operation centres (ESOCs). This will result in enterprises" hedging" cyber-risks arising from the lack of focus of such personnel to identify important indicators of cyber-compromise. Moreover, as a related but significant benefit, AI will help enterprises precisely identify the root cause of a cyber-attack from several compromise indicator features – something that is computationally infeasible for humans in ESOCs to routinely identify accurately and that too in the ever-increasing threat landscape. The last point is even more relevant today in the age of generative AI products such as ChatGPT that can create human-evading malware signatures on the fly.
2. In the process of generating effective true-positive cyber-attack alarms, AI has the power to dig out "complex" statistical relationships not only between compromise indicator variables (for both internal and external enterprise cyber-threats) but also between incidents (that might have occurred far in the past) that might look un-related to the gut-feeling driven human eye.
3. Unlike human intelligence, AI can effectively parse the entire space of structured, unstructured, and noisy threat-related data to output crisp and concise information needed for ESOC personnel to evaluate and optimise cyber-resilience metrics such as Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
4. While points 1, 2, and 3 above showcase the accuracy of AI solutions, speed is the other critically important factor distinguishing AI from human (expert) intelligence. The power of AI can be leveraged at speed, especially on real-time cyber-threat data, to conduct (real-time) data mining and (un-)supervised learning for generating accurate threat intelligence at speed. On an overarching note, AI will guide ESOC personnel (analysts) to fast, precise and automated cyber-resilience, improving incident response spanning an enterprise"s people, process, and technology spectrum.
The bottom line is that the Indian enterprise can save a lot more (probably a multi-fold of $1.2 million, as mentioned above) if it can leverage the power of AI to analyse and detect cyber threats accurately with low false alarms within a period much less than 200 days. This is simply because the existing cost estimates are conservative and exist only for reported threats, of which the reported quantity is far lesser than the actual number of threats reportable, and reducing reporting time is of essential financial value to an enterprise.
AI in Cybersecurity as a Competitive Business Strategy for Enterprises
It is common knowledge these days that AI is steadily penetrating virtually every process of an enterprise to align with the ultimate enterprise goal of increasing sales (and ROI). Cyber-security processes targeted towards improving enterprise cyber-resilience should be no different. More AI tools will imply better (quality) cyber-vulnerability data generation, better data will lead to better cyber-security management algorithms, better algorithms will lead to product services with higher cyber-security guarantees for client businesses, and subsequently, higher client adoption and the cycle should eventually culminate in increased sales.
A very good real-world example of this is the use of AI in its cyber-security processes by Trellix (erstwhile McAfee Enterprises) since 2020 to alert its customers (via their software products) on cyber threats, predict their impact, and prescribe corrective action. Since the use of AI as a cyber-security strategy on their High-Velocity Sales (HVS) platform, Trellix has boosted its initial potential client interests 10-fold, had a 5 percent increase in renewal rates, and had a three-fold increase in the amount of time managers could afford to spend to coach their sales team members on boosting sales.
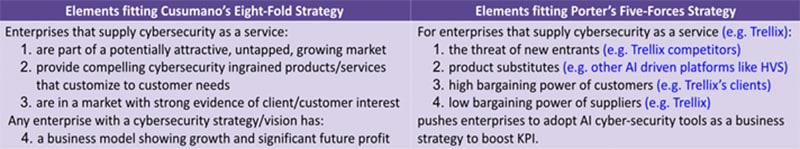
One might be inclined to believe (from the Trellix example) that the returns and competitive business risks of adopting and not adopting AI in cyber-security processes are quite high from a sales perspective. This point can be rationalised by seminal academic theory in the strategic management sciences. Based on insights from the widely popular Five Forces strategy model by Michael Porter of the Harvard Business School, the threat of new entrants (Trellix competitors), product substitutes (competitor products churned from AI-driven platforms like HVS), high bargaining power of customers (clients of Trellix-like products), and low bargaining power of suppliers (Trellix) should push enterprises to necessarily adopt AI as a cyber-security strategy to boost sales.
However, when it comes to enterprises (not necessarily only those having a cyber-security vision), it is not directly evident that incorporating AI as a cyber-resilience-improving strategy within business processes will boost sales—especially for small and medium businesses (SMBs). This is because
- (a) the bargaining power of clients is usually for high-featured service applications—the design of such applications often conflicts with cyber-security constraints, and
- (b) SMB managements in India often underestimate the likelihood and the financial impact of business disrupting cyber-incidents and overestimate the importance of selling high-featured client services that bypass effective cyber-security checks.
In the remainder of this article, we will provide the management and the board of enterprises in India (but not limited to) with an outline of a strategy to help them improve sales of services screened through AI-driven cyber-security processes.
A Strategic Outline for Enterprises to Decide Their "AI in Cyber-Security" Tool
We propose a strategic outline (a summary is provided through Figures 1 and 2), pivoted upon the type of service an enterprise offers to its clients, to determine the appropriate "AI in cybersecurity tool to boost both cyber-resilience and business KPIs (e.g., sales, ROI). The types of services an enterprise offers its clients could broadly have three flavours: transactional vendors hardware, software, and firmware suppliers and enterprises providing cybersecurity-as-a-service. First, the service provider, i.e., the enterprise, could be a transactional vendor offering services such as the use of point-of-sale (POS) products (e.g., retail stores). In such cases, the enterprise, to remain profitable and competitive (based on the traditional history of operation), should spend enough but not too much on security-boosting AI and related automation costs pertaining to the secure operation POS devices. An example of such an AI is Feedzai, an AI technology used across the banking industry to detect and prevent fraud by tracking behavioural and transactional patterns.
Second, the service-selling enterprise could be a hardware, software, and/or firmware supplier that has locked in a set of enterprises as customers (in a supply chain). One example of such an enterprise includes AWS, which provides a public cloud service as its business operation. Another example could include critical infrastructure enterprises reliant upon each other to sustain business continuity (e.g., a manufacturing company depending on a power grid and vice versa). In such cases, to prevent churn, remain profitable, and sustain market competition, the supplier enterprise must spend enough on AI to gather client environment data (applications, processes using supplied solutions) that "minimises" the likelihood of business disrupting malicious intruder entry into (IT/OT) systems. Essentially, the supplier enterprise must ensure their systems remain securely online to prevent business disruptions for both their clients and them by ensuring there is no malicious entry from any endpoint. An example of such AI is a real-time system orchestrated AI solution such as ScadaShield (by Cyberbit), that performs continuous monitoring and detection across the entire attack surface for both IT and OT components and can be combined with ESOC automation to trigger workflows that accelerate cyber-attack root cause identification and mitigation.
Third, the enterprise selling services could primarily be a solution consultant that provides its clients (e.g., general IT and/or OT-driven enterprises) security software as a service (SSaaS/SECaaS), where the selling enterprise (e.g., CrowdStrike, Trellix) can make profits, both out of the software/firmware/hardware components and their integration. In such cases, the enterprise must spend on AI that collects and analyses information within the supplying enterprise"s and client businesses" systems to prevent churn and remain competitively profitable in the market. The former protects the supplying enterprise from any malicious cyber intruders by analysing usage information and other data. In contrast, the latter protects the enterprise"s clients by analysing the client"s cyber posture information to generate effective alerts. The bottom line is that enterprises selling such products want to use AI to improve sales efficiency, improve customer relationships, and decrease costs. This requires the use of advanced AI tools to increase sales effectiveness. An example of such AI is that available on the XDR platform of Trellix that leverages AI, (real-time) machine learning, and advanced telemetry based on threat intelligence from more than one billion sensors across corporate and government enterprises to reduce malicious intruder probabilities and boost enterprise cyber-resilience significantly.
![]()
On top of everything, AI as a business strategy for the modern IT/OT-driven business ecosystems has the potential to adhere very well with certain elements of the seminal Eight-Fold strategy proposed by Michael Cusumano of the MIT Sloan School of Management for software-driven businesses—especially those offering pioneering solutions (cyber-security as a service). More specifically, enterprises providing cybersecurity-as-a-service
- (a) are part of a potentially attractive, untapped, and growing market where enterprises with good management are uniquely poised to make money for them (and their investors),
- (b) provide compelling cyber-security ingrained products and/or services that should necessarily customise to customer needs (different service types need customised AI solutions as discussed above in our arguments), and
- (c) provide services that have strong evidence of client/customer interest, catalysed by a solid working prototype/demo/security features that adhere to customer demands. Any enterprise with a cybersecurity strategy or vision has
- (d) a business model showing growth and significant future profits by inculcating AI as a cyber-security strategy/vision. However, the prerequisite to the success of AI in enterprises is also outlined by the Eight-Fold strategy: the enterprise needs
- (e) a good (technical/sales/marketing) management to drive the vision charted by AI as a cyber-security strategy and
- (f) a flexibility in strategy and product offerings to ensure enterprises adopting AI as a strategy can "jump" to adding/removing features based on dynamically changing customer demands.
![]()
Ranjan Pal and Cynthia Zhang contributed equally to the article.The authors would like to acknowledge Keri Pearlson of the MIT Sloan School of Management for her strategic insights from her research on cyber-security as a competitive business advantage.
Ranjan Pal (MIT Sloan School of Management, USA)
Cynthia Zhang (EECS, Massachusetts Institute of Technology, USA)
Bodhibrata Nag (Indian Institute of Management Calcutta, India)
Michael Siegel (MIT Sloan School of Management, USA)
This article has been published with permission from IIM Calcutta.
https://www.iimcal.ac.in/ Views expressed are personal.