An Atlas Of Internet Insecurity
Once relegated to the phreaks and nerds, cyberthreats now occupy a central place in the cultural conversation as the internet has become a more hostile place. Look at the growth in just one common sco


Rising Tide
Denial-of-service attacks are pummelling networks worse than ever, as hackers learn to force-multiply by digging into web infrastructure such as data centres. Attacks larger than 20 gigabits per second rose eightfold in 2013 compared with 2012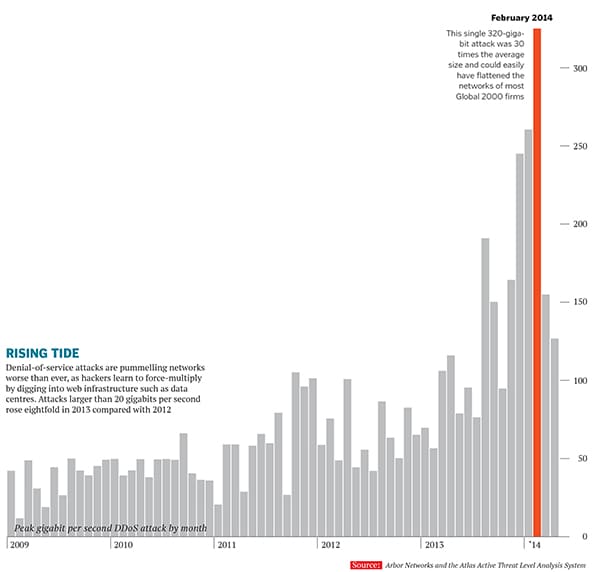 So what are we Going to do about it?
So what are we Going to do about it?
Ten cyberexperts offer up their best ideas for stemming the threats we face. Note: Almost every one of them muttered something about there being no silver bullets Brian Krebs
Brian Krebs
Investigative reporter and author of the upcoming book Spam Nation
“Being safe and secure online fundamentally requires a mindset shift. I’d like to see more internet users place far less reliance on automated tools for security and take a defensive posture that begins with an appreciation that everything can be hacked but that bad guys are mostly after information of value that isn’t adequately protected. This means educating oneself about the limitations of security tools and taking proactive steps to shore up these defences.”
Scott Charney
Corporate Vice President, Trustworthy Computing Group, Microsoft
“In the world of cloud services and Big Data, people expect that companies will be responsible stewards of that data. Indeed, having trust in a provider will ultimately determine if people are willing to use connected products and services. Because of this, companies must be transparent about how they handle data, ensure they have robust corporate programmes to protect privacy and ultimately be accountable for their actions.” Chris Young
Chris Young
svp, Security Business Group, Cisco
“Each connection in the Internet of Things brings new risks that challenge defenders to provide enhanced levels of protection. This requires a threatcentric approach to security, with solutions that work together, collecting and sharing intelligence, with a coordinated focus on threats. This is the only way to protect what matters most. With the Internet of Things every company becomes a technology company, and every company becomes a security company.” Chad Sweet
Chad Sweet
CEO, The Chertoff Group, a security and risk advisory firm
“Corporate America rarely grows 100% organically anymore. M&A is almost always involved. Increasingly, when you acquire a company, you inherit all of that company’s cybersins. If their systems are infected or breached, you’re infected. In the same way a financial audit is done to make sure the books aren’t cooked, there needs to be a cyberaudit to give stakeholders confidence that the key, valued intellectual property they are purchasing for future revenue has not been compromised.” Edith Ramirez
Edith Ramirez
Chairwoman, Federal Trade Commission
“Businesses should encrypt sensitive data. Encryption, properly implemented, is becoming more important. That applies to sensitive information across the board. Online security for children’s information is of particular concern. The Children’s Online Privacy Protection Act gives parents the right to control the collection of personal information from their kids. If parents okay the collection, the website or app must provide reasonable security for the information, or risk
a fine from the Federal Trade Commission.”
Throw weight
Here’s a look at which countries hit one another most often (or at least where the hackers pretend to be coming from). The battle lines are not easily drawn. The USA and China are under the heaviest attack and are also the countries from which the most cybergrenades are thrown. Percentages are the portion of total attacks from the originating nation.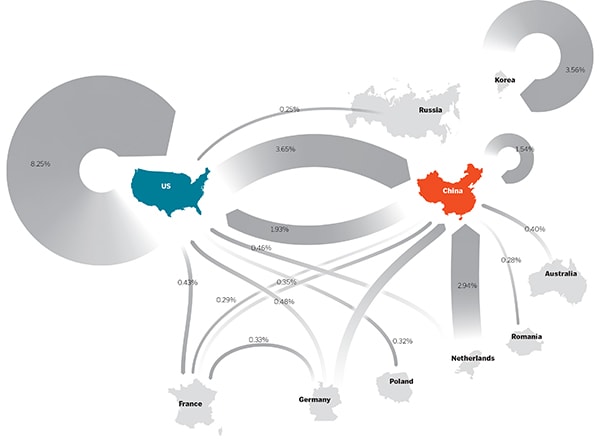
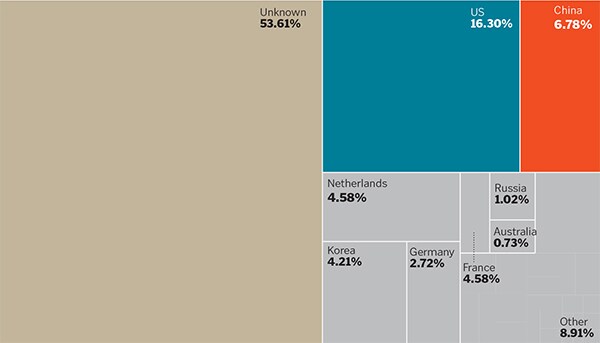 And You Thought China was Bad
And You Thought China was Bad
Countries that originated (above) and received (below) the most denial-of-service attacks over 1 gigabit per second in the past 12 months. The huge unknown category underscores the difficulty in tracking down the origins of attacks, which can bounce from off shore servers.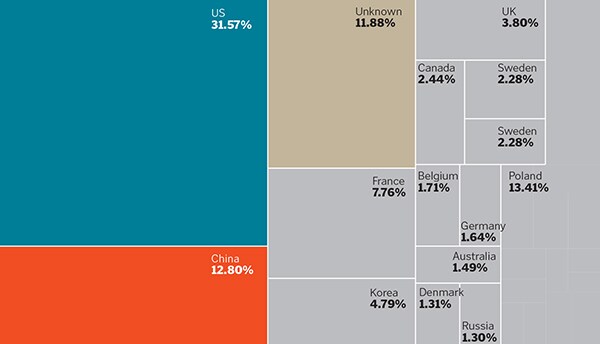
 Heather Adkins
Heather Adkins
Manager, information security, Google
“For the last 20 years we’ve been playing catch-up to fix operating systems that were designed in the 60s and 70s. We need to rethink that from the ground up. For instance, instead of running lots of different programs and apps, we should have users work with a single interface, like a browser, through which they can do multiple things. That will keep the attack surface smaller: If you have a big castle , it’s hard to defend, but if you have a smaller castle, it’s easier.”
Daniel Suarez
Sci-fi writer, author of Daemon and Influx
“The internet wasn’t intended to be a secure network, yet it’s been pressed into service for online banking, stock trading, industrial process control systems and more. What we need is an Apollo-like national project to build a new, secure network for critical infrastructure that would use a separate protocol, proprietary hardware, dedicated fibre-optic lines and powerful encryption to eliminate all but the most elite interlopers. This wouldn’t replace the internet it would only be used where identity and trust are critical.” Chris Soghoian
Chris Soghoian
Principal Technologist, Aclu
“For all the talk in Washington of the importance of cybersecurity, there is no agency in the government that is directly responsible for consumer cybersecurity and making sure regular Americans are secure. There’s no one forcing companies to patch vulnerabilities to protect their users... we’re all running out-of-date software and companies are storing far too much of our sensitive data in insecure ways. We need a powerful privacy and data-security regulator [to] set data security rules for companies and enforce them.” Joe Sullivan
Joe Sullivan
Chief security officer, Facebook
“When core internet technologies are well-maintained, the internet works. When they fail, the best-laid security plans collapse. If we’re going to prevent future heartbleeds, we need security infrastructure to keep up with billions more coming online. As an industry, let’s invest in technologies that secure mobile networks, data-centre traffic, and the websites and apps people access every day. We have to make it easier for future developers from anywhere to choose secure options from the start.”
Data Graphics By Maxwell Henderson
Illustrations By Patrick Welsh
The FBI got little buzz last year when it debuted its cybercriminal most wanted list. Things got serious when the bureau put five Chinese army officers atop the list Since 1950, the Federal Bureau of Investigation (FBI) has plastered US post offices with mug shots of America’s worst outlaws. The iconic most wanted list first went online in 1995, and since then the bureau has solved 66 cases as a direct result of posting faces on the web. It took until last November, though, for the FBI to acknowledge fully the era we live in by prominently publishing online its most wanted list of cybercriminals.
Since 1950, the Federal Bureau of Investigation (FBI) has plastered US post offices with mug shots of America’s worst outlaws. The iconic most wanted list first went online in 1995, and since then the bureau has solved 66 cases as a direct result of posting faces on the web. It took until last November, though, for the FBI to acknowledge fully the era we live in by prominently publishing online its most wanted list of cybercriminals.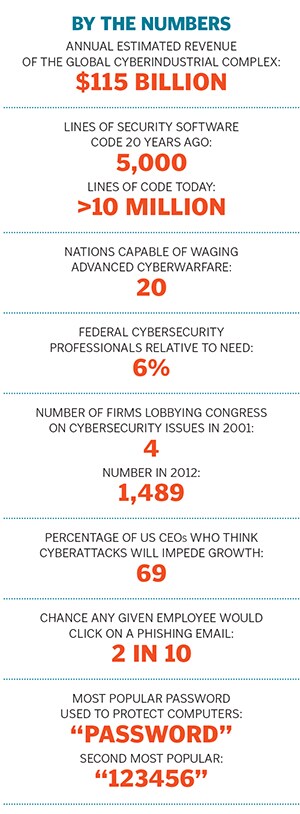 The original list didn’t get much buzz, as it was dominated by the expected shifty-looking East European credit card scammers. A standout on the list (though it’s not ranked) was Bjorn Daniel Sundin, a 35-year-old fugitive from Sweden indicted in 2010 for running a $100 million bogus-software scam. Then, last month, the FBI shook things up by putting on the list five officers of China’s People’s Liberation Army. The officers had just received fresh indictments on 31 criminal counts for their alleged roles in hacking into Westinghouse Electric, Alcoa, Allegheny Technologies, US Steel, The United Steelworkers Union and SolarWorld. Chinese officials denounced the charges, calling out the US for its spying.
The original list didn’t get much buzz, as it was dominated by the expected shifty-looking East European credit card scammers. A standout on the list (though it’s not ranked) was Bjorn Daniel Sundin, a 35-year-old fugitive from Sweden indicted in 2010 for running a $100 million bogus-software scam. Then, last month, the FBI shook things up by putting on the list five officers of China’s People’s Liberation Army. The officers had just received fresh indictments on 31 criminal counts for their alleged roles in hacking into Westinghouse Electric, Alcoa, Allegheny Technologies, US Steel, The United Steelworkers Union and SolarWorld. Chinese officials denounced the charges, calling out the US for its spying.
No one honestly expects the FBI’s move to result in the arrest of senior Chinese military officers. “But this places a significant amount of pressure on them,” says Michael Quinn, a former FBI agent and currently associate managing director at Kroll, an investigations firm. “If the FBI continues to indict individuals from China, I tend to think they will have fewer individuals willing to conduct this kind of cyberespionage.”
The naming and shaming of Chinese soldier-spies shows America’s resolve, not to mention technical chops, at snooping out the snoops. FBI cyberforensics specialists collected evidence by “spying right back to the very [Chinese] government facility, desk, keyboard and specific government-trained hacker,” says Steven Martinez, a former FBI agent and now managing director of Stroz Friedberg, a New York City firm that investigates network breaches. “This directly reflects what I know to be the FBI’s highest priority within its cyber programme—namely, to address threats from sophisticated, state-sponsored actors,” he says.
The five officers were part of Unit 61398, allegedly a cyberespionage wing of the People’s Liberation Army. They were caught systematically pilfering design and technical specifications, sensitive emails and financial information from 2006 through April 2014. A recent report from digital forensics firm crowdstrike outlines evidence of a much larger Chinese-sponsored spying collective that includes other military cyberspying units as well as loosely knit contractors.
At the very least, the notoriety from being on the list ought to put a crimp in overseas travel plans for the accused, who now face the risk of being identified, arrested and extradited, says Martinez. Meanwhile, the bureau’s cyberlist gains more lustre, something that can only reinforce the slow but steady progress being made in coordinating investigations across borders to stop bad guys. —BA
First Published: Jul 25, 2014, 06:25
Subscribe Now