The Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021, which the government of India notified on February 25, were supposed to provide clarity on whether or not breaking end-to-end encryption is a limit that platforms must breach to enable traceability. Instead, even two weeks after the Rules have been notified, there is no clarity on what they mean for end-to-end encrypted messaging platforms.
Much of the debate around “enabling the identification of the first originator” or traceability on end-to-end encrypted platforms has circled around whether it is possible to identify the originator of a message without breaking or diluting end-to-end encryption. So much so that a crucial case on enabling traceability on WhatsApp, which got transferred to the Supreme Court from the Madras High Court, spent at least four hearings discussing whether or not traceability was possible without breaking end-to-end encryption. In the last hearing in January 2020, notification of these Rules was still awaited. The case is still pending.
The Indian government has maintained that it is indeed possible. However, WhatsApp, Signal, privacy advocates and other cryptography experts have vehemently said that enabling identification of the originator at the very least defeats the purpose of end-to-end encryption if not entirely breaks it.
The Indian government has thus far been proposing two schemes as potential solutions to the problem of identifying the originator: Tagging each message with the originator’s information (as proposed by IIT Madras’s Dr V Kamakoti) and comparing hash values of problematic messages with what WhatsApp/intermediary has (as discussed by Rakesh Maheshwari from the Ministry of Electronics and Information Technology [MeitY] at multiple public events).
Moxie Marlinspike, creator of the Signal protocol and CEO of Signal Messenger, told Forbes India a fortnight before the Rules were notified that “Signal is designed so that Signal does not know who is messaging who. Signal doesn’t have that information.” On traceability, he said that end-to-end encryption and traceability cannot co-exist. “There is no way to have data privacy for everybody but just a specific set of people. [Once you make it possible] to just give the police access to data under some set of circumstances, anyone can get access to that data.”
What is end-to-end encryption?
E2EE creates a secure, encrypted communication channel between two users that can never be intercepted. When, say, Alice and Bob communicate, both of them generate a public key and a private key. The former is visible to all others in the WhatsApp server and is necessary to start the communication. The private key is used to access their own messages and is known only to their devices. When Alice sends a “Hello” to Bob, it is encrypted in such a way that it can only be decrypted using a key which exists only on Alice and Bob’s devices. And this unique key keeps changing with every message sent.
Signal Protocol, which is used by WhatsApp, Signal, and by Facebook Messenger and Skype for secret chats, is the most used end-to-end encryption protocol. Apple’s iMessage is also an end-to-end encrypted messaging service but it uses a different protocol.
![traceability-1 traceability-1]()
What is traceability?
The phrase “shall enable tracing out of such originator” in the draft amendments was replaced with “shall enable the identification of the first originator” in the notified Rules. According to the Information Technology Act, 2000, an originator is defined as “a person who sends, generates, stores or transmits any electronic message or causes any electronic message to be sent, generated, stored or transmitted to any other person but does not include an intermediary”.
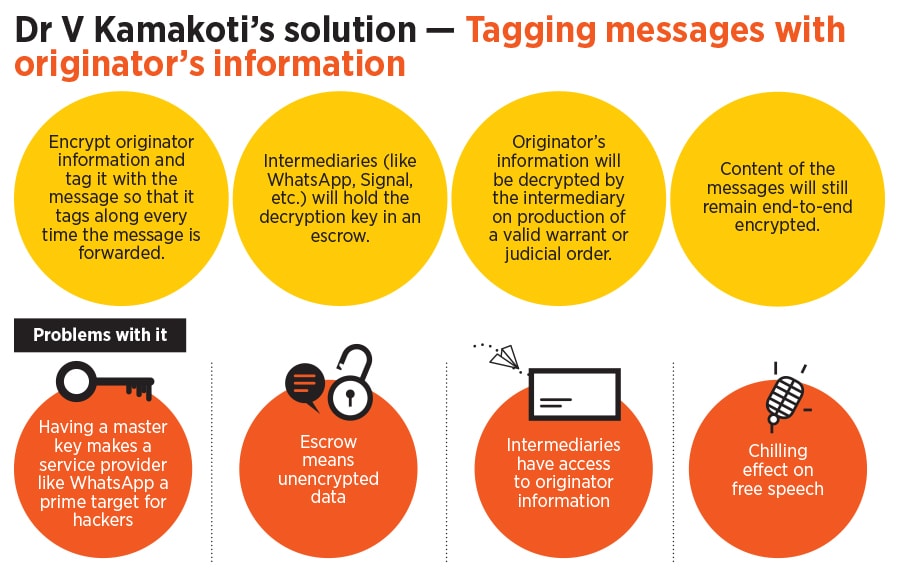
The Kamakoti Solution: Tagging the message with originator’s information
In May 2019, at the Madras High Court’s directions, the then Chief Secretary of the Tamil Nadu government, Dr Girija Vaidyanathan, had convened a meeting between the Tamil Nadu police and social media intermediaries. It is at this meeting that Dr V Kamakoti, a computer science professor at IIT Madras and a member of the National Security Advisory Board (NSAB), had suggested that WhatsApp should consider including the phone number of the originator of the message every time it is forwarded.
This suggestion culminated in Kamakoti’s official affidavit to the court, which has shaped much of the debate around traceability in India. In fact, language similar to what Kamakoti has used in the affidavit, where emphasis has been laid on not decrypting the content of the message itself, has found itself space in the Rules as a proviso.
Kamakoti proposed two levels of encryption. The message “Hello” remains encrypted as it is now, while the originator’s information gets tagged along with the “Hello” in an encrypted manner every time the message is forwarded. The decryption key to the originator information, in this schema, is retained in an escrow with WhatsApp (think Blackberry’s encryption model). Once a problematic message is reported to a law enforcement agency, the latter goes to WhatsApp with the message and WhatsApp uses its key to decrypt the originator’s information. The decryption can happen only if relevant court orders are produced by the law enforcement agencies.
In an interview with MediaNama in 2019, Kamakoti had explained that there are two things to consider—tagging messages as forwardable or not-forwardable, and who is the originator. For the former, he said that the originator of the message should have the option of marking each message as “forwardable” or “not forwardable” as a method of giving consent. In the former case, the originator assumes responsibility for the message and their originator information gets attached to the message. If a recipient forwards/sends a “not forwardable” message, the recipient then becomes the originator.
It is only in the case of simple forwards that the originator information travels along with the message. If a recipient copy pastes the text, they essentially change it and become the originator. If the recipient takes a screenshot and sends it, they become the originator. In case of a media file, if a recipient adds a comment to it, they become the originator, as per Kamakoti’s proposal.
Kamakoti’s proposal was decried by WhatsApp, cryptographic experts and advocates of privacy and free speech. In its response to the court, WhatsApp had submitted that Kamakoti’s proposal would “wholly undermine its [WhatsApp’s] end-to-end encryption as users would be afraid to freely express themselves if their private thoughts would forever be linked to their identities”.
Problems included falsely labelling someone as the originator even though they found that content on other platforms or elsewhere and copied it from there. This is a problem that Google, too, had highlighted during the proceedings in Madras High Court—the counsel for Google had said that even for YouTube, finding the originator was difficult as the originator of the content is not necessarily the first person who created the content itself, and potentially on another platform.
WhatsApp had also submitted that in the attempt to get to the originator, innocent people may get caught as savvier criminals would use modified versions of the app to potentially frame others. Modified versions of apps are very common wherein they are sideloaded (downloaded from the internet directly onto phones without being mediated through official app stores) and features are cherry-picked as per the user’s convenience. It is practically impossible for all official developers, not just WhatsApp, to shut down every such modified app.
WhatsApp had also said that often forwarded messages do not give the context that may have accompanied the original message, thereby skewing the intent and meaning of the message itself.
![debayan gupta-quote debayan gupta-quote]()
A bigger problem is that storing a master key for the originator information makes WhatsApp a prime target for hackers and defeats the purpose of data minimisation.Forbes India has a copy of WhatsApp’s submission.
Digital rights organisation, the Internet Freedom Foundation, which is an intervener in the traceability case, too had submitted a technical affidavit against Kamakoti’s proposal. Authored by IIT Bombay’s Dr Manoj Prabhakaran, a computer science professor who specialises in cryptography, the affidavit said that not only did traceability erode all users’ privacy, it also was not an effective means of fighting fake news. He had warned that adding a digital signature to every message would have a “chilling effect on the right to free speech”. He had instead proposed a feature that could allow users to anonymously send viral messages to a server and make them publicly available.
All proponents of end-to-end encryption have argued that traceability undermines the right to communicate anonymously on the internet, a feature that makes it easier for human rights activists, dissenters, people belonging to vulnerable and marginalised groups to be targeted by authoritarian states, malicious actors, and those in power.
In an interview with Forbes India before the Rules were notified, in response to a question about the feasibility of Kamakoti’s solution, Signal’s Marlinspike had said, “Anytime someone says something about escrow that just means that it is unencrypted. It is the same situation where you either have one or you don’t. Signal has been meticulously designed to keep your data in your hands instead of ours.” He mentioned how there are two ways of looking at security—computer security which is a “losing strategy for the last 30 years”, and information security wherein “information itself is encrypted”. The latter means that if they are stored on computers and computers cannot be secured, it does not matter as the information itself is secure.
“I don’t think Prof. Kamakoti’s suggestion as stated is currently feasible. This is very definitional. When cryptographers say end-to-end encryption, we mean a very particular thing where to anyone except the sender and the receiver, messages should look like garbage, and an outsider should not be able to tell [beyond just traffic analysis] which message was sent to whom,” Dr Debayan Gupta, an assistant professor of computer science at Ashoka University, tells Forbes India.
Gupta warns that the moment there is something that is sent along every message which can be tracked by WhatsApp, the definition of end-to-end encryption breaks. “In an ideal end-to-end encrypted scenario, if there are two messages that I can send to you, WhatsApp should not be able to know which message I sent to you,” he says.
![traceability-4 traceability-4]()
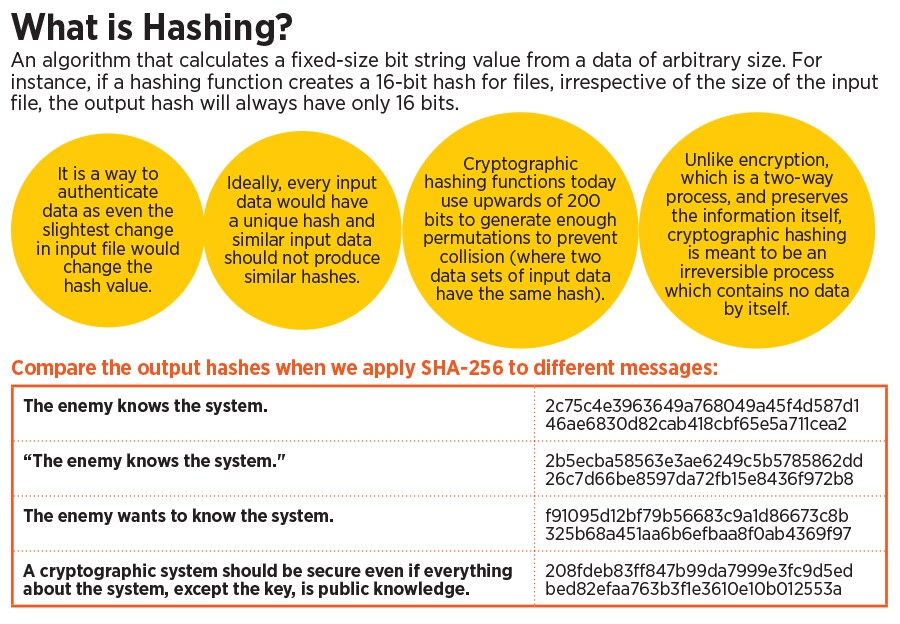
Tracing the originator through a catalogue of hashes
At an online event organised by the Internet Society and the CCAOI after the Rules were notified, Rakesh Maheshwari, the group coordinator for cyber laws at MeitY, proposed another solution. The idea is that when a user approaches a law enforcement agency with a problematic message, the law enforcement agency can go to WhatsApp and ask the platform to search for the hash in a catalogue of hashes to find the originator. Maheshwari’s assumption is that forwarded messages whose content does not change would have the same hash.
Hashing is a mathematical function through which the integrity of data is ascertained. For instance, if I write “hello” and run a hashing function on it, it may be hashed as A$F. The slightest change in the input data—“HEllo” instead of “hello”—would result in a change in hash. This technique is also used in digital forensics to ensure that digital evidence, such as a hard drive, has not been tampered with. When a hard drive is seized, it is immediately hashed and the hashes are shared with both the prosecution and the defence. At a later date, if either side wants to confirm the integrity of the hard drive in question, they hash the hard drive again. A change in a single character of the hash would mean that the hard drive has been tampered with.
![traceability-6 traceability-6]()
Gupta warns that the solution proposed by Maheshwari is not feasible. That is because when a hash is generated for a message in an end-to-end encrypted platform, it takes into account the unique identity keys of that particular sender and receiver in addition to the encrypted message itself.
This means, the hash value of a “Hello” that Alice sends to Bob is different from the hash value of “Hello” that Bob sends/forwards to Charlie. If Charlie were to go to the police with the “Hello” that Bob sent to him, even if WhatsApp could search for the hash generated, it would only lead to one message—the one between Bob and Charlie. Alice will not turn up. The only way WhatsApp could make Alice turn up is if it breaks its “double ratcheting” algorithm that changes the key between two users for every message in a feature that is called “forward secrecy”. Moreover, because Alice and Bob’s keys keep changing with every message, even if Alice were to send Bob “Hello” twice, both will have different hashes.
![traceability-3 traceability-3]()
Gupta warns that this means WhatsApp will be able to track all the messages that people send on its platform, thereby defeating the entire purpose of end-to-end encryption. Furthermore, this means that WhatsApp will retain entirely too much (meta) data, thereby defeating the privacy-preserving principle of data minimisation.
![traceability-5 traceability-5]()
OTR deniability means you can’t get to the originator
Signal Protocol, which is the one that WhatsApp uses to implement end-to-end encryption, also offers off-the-record deniability, better known as OTR deniability. When Alice sends Bob a message “Hello”, Alice locks the message in a box (let’s call this “encryption”) with a key, which is unique to this particular message between Alice and Bob which no one else knows, and Alice signs the outside of the box. To anyone else who tries to get to the message (interception), they will only see a random string of characters because of the encryption at play. Bob, who is the only one who has a copy of that unique key, on receiving the box (encrypted message), is sure that it has come from Alice. But, later on, Bob cannot prove to anyone else that Alice sent that particular message: Because the signing key was derived from a value shared by Bob. Once Bob receives the message, he also has the ability to change/forge it himself if he has enough technical know-how.
![traceability-2 traceability-2]()
Gupta explains that such technical know-how is quite common. “Many of my undergraduates can do these things,” he says. Once messages are decrypted, they are stored in the local databases of the smartphone where they can be accessed by rooting the device. Think of it as getting admin access to your smartphone. Then, Bob can change the message “Hello” from Alice to “Hello, you are a buffalo” because he has access to that unique key.
Gupta explains that the user need not have the technical ability themselves either. That is because there are multiple variants of WhatsApp that are available for people to sideload. These copies still use the Signal Protocol because of which they can still use the E2EE offered by WhatsApp, but they pick and choose the other features of the app client itself.
Other solutions like digital signatures have limitations
A cryptographic expert who spoke to Forbes India on the condition of anonymity said that originator tracing might not be the best way to thwart malicious viral messages. “But if that is the path one chooses, then a reasonable way to implement it without affecting much else—including end-to-end encryption—is to require a digital signature of an Indian originator to be attached to any message intended for a large audience,” he says. If a message is sent to a group without this signature, it will not be shown to the recipients it could be shown in on-to-one messaging but would not be forwardable. This is a slightly more refined version of what Kamakoti had proposed.
“While international (or reverse-engineered) versions of the app can originate a message without attaching a signature, they will not be forwarded further by the legitimate Indian installations of the app, thereby preventing them from going viral in India,” he further explains. Indian users would be able to forward an unsigned message by explicitly choosing to become the originator, maybe through a pop-up informing them about the Rules and them becoming the originator and thus liable for the message.
Here, the expert warns that the digital signatures must also be end-to-end encrypted so that WhatsApp servers cannot distinguish between signed and unsigned messages.
“When a viral message is caught in the wild with a signature, the authorities can collaborate with WhatsApp to trace the signer of the message to a WhatsApp account. The cryptographic security of digital signatures would guarantee that the message was indeed endorsed by the identified WhatsApp account, unless their device was compromised. However, an individual may still be framed if their identity was used to acquire the phone number registered with WhatsApp,” he adds.
Having said this, the expert also warns that this move would have a massive chilling effect on free speech, “disproportionate to the goal of tracing the source of viral messages”.
Also, digital signatures must be allowed to expire. Without such expiration date, “old messages can be revived several years down the line, in a different context”. “Secondly, to be able to trace the originator in such a case, WhatsApp will have to retain all the public keys all the (Indian) users ever used, forever. This would be problematic as keys need to be frequently renewed for security and privacy purposes,” experts say.
Does it solve the problem?
Both Gupta and the anonymous expert concurred that traceability barely solves the problem of getting to people who systematically spread malicious information. Instead, it would keep netting less digitally savvy folks for not being media literate enough.
One of the biggest issues, of course, is how do you establish beyond doubt that the first originator is indeed the first person within the physical territory of India to send the message. What happens if people use VoIP [Voice over Internet Protocol] numbers and VPNs [Virtual Private Networks] through which they neither have a +91 number, nor an Indian IP address connected to their user account? What if someone with a +91 number immigrates to the US and retains their old WhatsApp or Signal account? Would they be held responsible? Beyond VPNs, it is very easy to spoof IP addresses and location data. “Children were doing this when they were attempting to catch Pokémon,” Gupta jokes.
Gupta also warns that the Rules don’t take into account the global nature of communication over internet-based apps. If there are two versions of WhatsApp—one for India and one for the rest of the world—, “it is not clear how you would change that protocol at the edges of this geographical entity called India”. “How would that cross-protocol communication happen?” Gupta asks. He reminds that “the Internet is not a sovereign territory” to which “territorial sovereign laws” can be easily applied. “The originator of the information bit needs to be cleared up very carefully,” he says.
Even if WhatsApp and Signal were to somehow introduce traceability, the actual criminals would move to other platforms that have not attracted similar kind of regulatory scrutiny. It is important to remember that the traceability rule only applies to significant social media intermediaries, that is, only platforms that have more than 50 lakh users. If petty criminals, members of organised crime, and professional propagators of misinformation move to smaller apps, they are as it is not covered by the Rules.
“Before we break this beautiful protocol and technology and build patches for it, we as cryptographers want to make sure we understand what the requirements are,” says Gupta, adding that this discussion should have happened before the Rules were notified, not after.
(Watch out for part 2 of the series tomorrow, which will look at what the government can legally ask with respect to encryption, and what the law enforcement has to say about the identifying the originator.)

 Image: Shutterstock Illustrations: Sameer Pawar
Image: Shutterstock Illustrations: Sameer Pawar